Permissions
Learn about StarOps Permission Requirements
Integration Permissions Overview
StarOps can integration with both Amazon (AWS) and Google Cloud (GCP) as intrafstructure providers. You will find the related permissions leveraged for both listed below. It is important to note that, by default, integrations to your cloud account will start as READ ONLY. StarOps will only take advantage of full R/W capabilities once you upgrade the integration to that level. Until you have done so, only read queries can be performed against your cloud account.
AWS - IAM Policy Permission
For StarOps to perform various workflows across your AWS Cloud Infrastucture it will require certain permissions. This is provided via automatic IAM Policy setup.
Leveraging CloudFormations, the setup of these IAM policy permissions is a simple process from the Integrations section of StarOps.
By default, your account integration will start in READ ONLY mode.
This will be signified with the Read Only tag you will see on your integration screen:
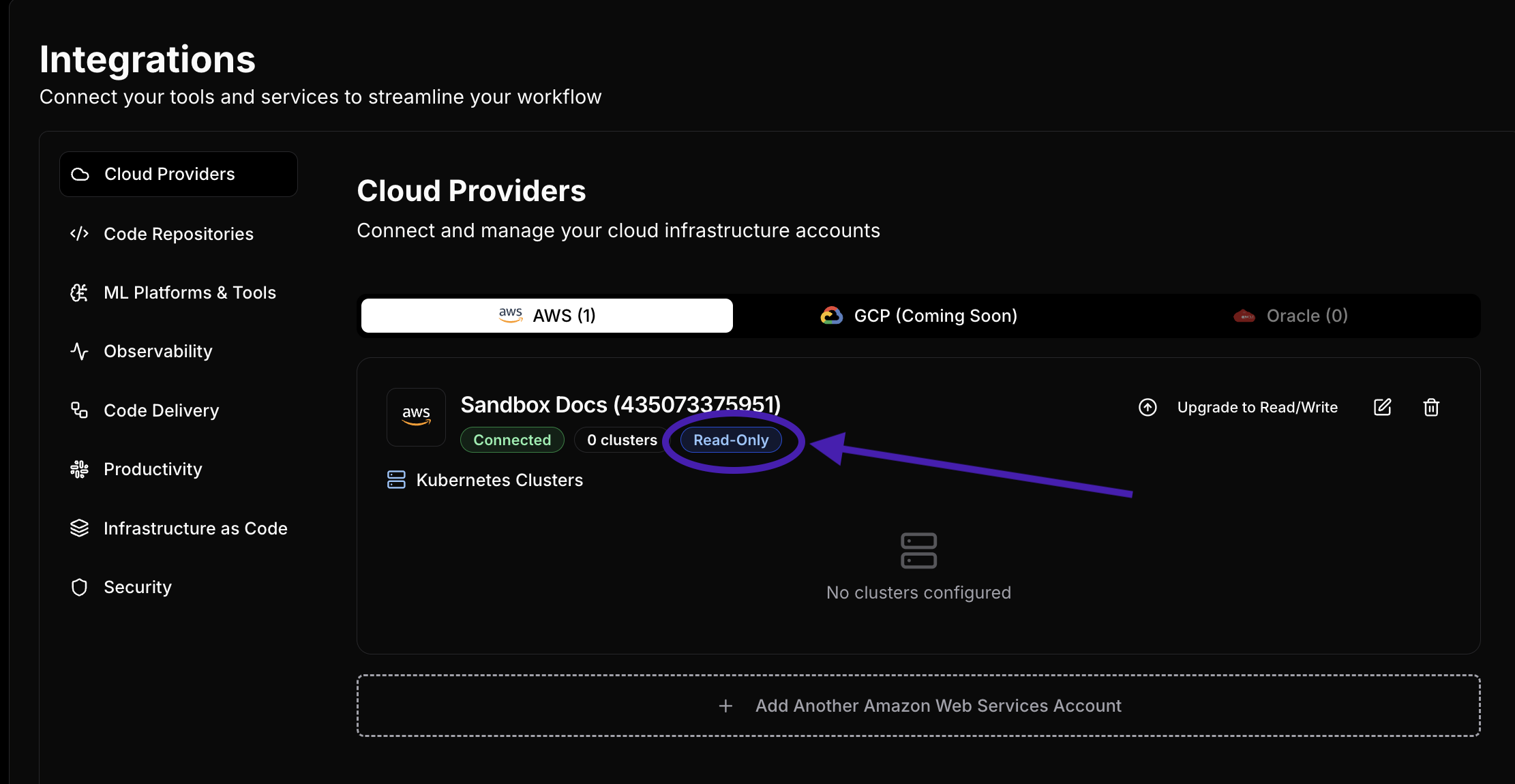
Any StarOps feature that you request without such upgrade will prompt you accordingly like this:

If you are interested in full StarOps provisioning capabilities on your behalf, you can upgrade any read only integration to READ/WRITE, by selecting the Upgrade option on the integration screen for any account:
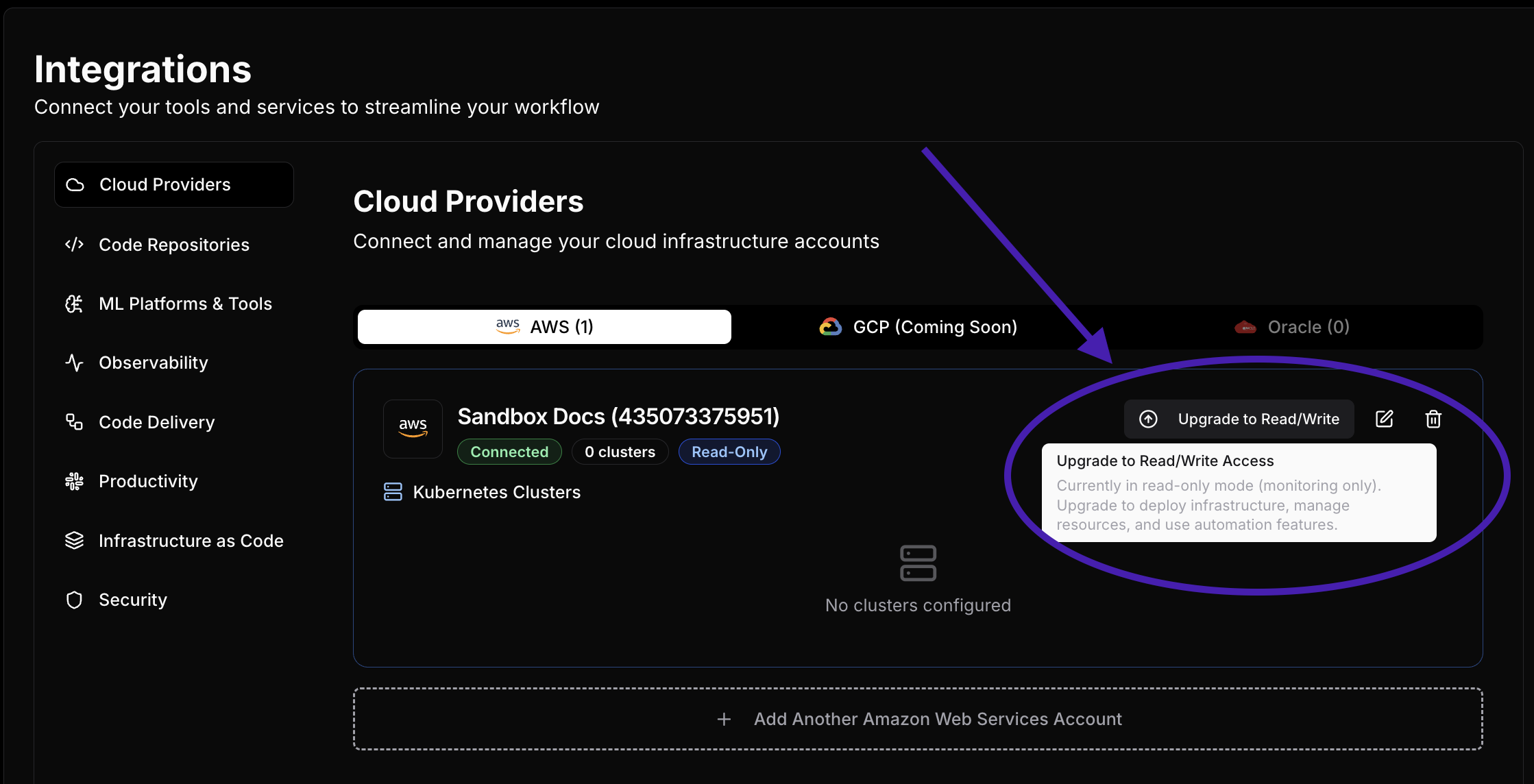
FULL READ/WRITE IAM Permissions (as on 10/15/25)
(Get and List Permissions only for Read Only integrations)
iam:CreateRole- Creating new IAM roles for service accounts and applicationsiam:GetRole- Checking existing role configuration before modificationsiam:DeleteRole- Cleaning up unused roles during resource deprovisioningiam:ListRoles- Discovering existing roles for inventory and managementiam:UpdateAssumeRolePolicy- Modifying trust relationships for role accessiam:PutRolePolicy- Attaching inline policies to roles for specific permissionsiam:GetRolePolicy- Reading current role policies before modificationsiam:DeleteRolePolicy- Removing unnecessary policies during cleanupiam:ListRolePolicies- Listing all policies attached to a roleiam:CreatePolicy- Creating custom policies for specific use casesiam:GetPolicy- Checking policy details before attachmentiam:GetPolicyVersion- Reviewing specific policy versionsiam:ListPolicyVersions- Managing policy version historyiam:DeletePolicy- Removing obsolete policiesiam:CreateUser- Creating IAM users for service integrationsiam:GetUser- Retrieving user information for access managementiam:DeleteUser- Removing users during deprovisioningiam:ListUsers- Inventorying existing usersiam:CreateAccessKey- Generating access keys for programmatic accessiam:ListAccessKeys- Managing user access keysiam:DeleteAccessKey- Rotating or removing access keysiam:AttachUserPolicy- Granting permissions to usersiam:DetachUserPolicy- Removing permissions from usersiam:DeleteUserPolicy- Cleaning up user-specific policiesiam:ListAttachedRolePolicies- Auditing role permissionsiam:ListAttachedUserPolicies- Auditing user permissionsiam:ListGroupsForUser- Checking user group membershipsiam:ListInstanceProfilesForRole- Managing EC2 instance profilesiam:ListAccountAliases- Retrieving account information for identificationiam:*- Full IAM access for comprehensive identity management
S3
s3:ListAllMyBuckets- Discovering existing S3 buckets for inventorys3:CreateBucket- Creating new buckets for data storage and model artifactss3:DeleteBucket- Cleaning up unused buckets during resource deprovisionings3:ListBucket- Listing objects within buckets for content managements3:GetBucketLocation- Determining bucket regions for compliance and optimizations3:PutBucketPolicy- Configuring bucket access policies for securitys3:GetObject- Retrieving files, models, and configurations from bucketss3:PutObject- Uploading models, data, and configuration filess3:DeleteObject- Removing obsolete files and cleaning up storages3:HeadObject- Checking object metadata without downloading contents3:*- Full S3 access for comprehensive storage management
EKS
eks:ListClusters- Discovering existing Kubernetes clusterseks:DescribeCluster- Retrieving cluster configuration and statuseks:CreateCluster- Provisioning new Kubernetes clusterseks:DeleteCluster- Decommissioning clusters during cleanupeks:UpdateClusterConfig- Modifying cluster settings and configurationseks:UpdateClusterVersion- Upgrading Kubernetes versionseks:AccessKubernetesApi- Interacting with Kubernetes API for workload managementeks:CreateAccessEntry- Managing cluster access for users and serviceseks:DeleteAccessEntry- Removing cluster access during deprovisioningeks:AssociateAccessPolicy- Granting specific permissions within clusterseks:DisassociateAccessPolicy- Removing permissions from cluster accesseks:ListAccessEntries- Auditing cluster access permissionseks:ListAccessPolicies- Reviewing available cluster policieseks:*- Full EKS access for comprehensive cluster management
EC2
ec2:DescribeInstances- Inventorying EC2 instances for resource managementec2:DescribeVpcs- Discovering network configurations for deployment planningec2:*- Full EC2 access for comprehensive compute and networking management
Route53
route53:ListHostedZones- Discovering DNS zones for certificate managementroute53:ListHostedZonesByName- Finding specific DNS zones by nameroute53:GetHostedZone- Retrieving DNS zone configuration detailsroute53:ListTagsForResource- Checking DNS resource tags for organizationroute53:CreateHostedZone- Creating new DNS hosted zones for domain managementroute53:DeleteHostedZone- Removing DNS hosted zones during cleanuproute53:GetChange- Checking the status of Route 53 change requestsroute53:ChangeResourceRecordSets- Modifying DNS records within a hosted zoneroute53:ChangeTagsForResource- Managing tags on Route 53 resourcesroute53:*- Full Route53 access for comprehensive DNS management
CloudFormation
cloudformation:DescribeStacks- Checking stack status and outputscloudformation:DeleteStack- Cleaning up CloudFormation stackscloudformation:*- Full CloudFormation access for infrastructure management
Lambda
lambda:ListFunctions- Discovering existing Lambda functionslambda:InvokeFunction- Triggering webhook and notification functionslambda:DeleteFunction- Cleaning up Lambda functions during deprovisioning
CloudWatch Logs
logs:CreateLogGroup- Setting up logging for applications and serviceslogs:CreateLogStream- Creating log streams for organized logginglogs:PutLogEvents- Writing log entries for monitoring and debugginglogs:*- Full CloudWatch Logs access for comprehensive logging management
CloudFront
cloudfront:Get*- Retrieving CloudFront distribution configurations, cache behaviors, and settingscloudfront:List*- Listing CloudFront distributions, invalidations, and origin access controls
DynamoDB
dynamodb:List*- Listing DynamoDB tables, backups, and global tables for inventorydynamodb:Describe*- Retrieving table metadata, configurations, and status informationdynamodb:GetItem- Reading individual items from DynamoDB tablesdynamodb:BatchGetItem- Reading multiple items efficiently from tablesdynamodb:Query- Querying tables using partition and sort keysdynamodb:Scan- Scanning entire tables for data analysisdynamodb:ConditionCheckItem- Checking item conditions without modifying datadynamodb:ListTagsOfResource- Retrieving tags associated with DynamoDB resources
Service Quotas
servicequotas:GetServiceQuota- Checking current service quota limitsservicequotas:ListServiceQuotas- Listing all service quotas for planningservicequotas:RequestServiceQuotaIncrease- Requesting quota increases for scaling
Other Services
RDS
rds:DescribeDBInstances- Discovering database instances for inventoryrds:Describe*- Full read-only access to RDS metadata, snapshots, and parametersrds:ListTagsForResource- Retrieving tags associated with RDS resources
ECR Public
ecr-public:*- Full ECR Public access for container image management
KMS
kms:*- Full KMS access for encryption key management
EventBridge
events:*- Full EventBridge access for event-driven architecture
SQS
sqs:*- Full SQS access for message queue management
Organizations
organizations:*- Full Organizations access for account management and information
STS
sts:GetServiceBearerToken- Obtaining service tokens for authentication
Comprehensive Read-Only Access
Security Services
guardduty:Get*,guardduty:List*- GuardDuty threat detection datainspector:Describe*,inspector:Get*,inspector:List*- Amazon Inspector vulnerability assessmentsmacie:Get*,macie:List*- Amazon Macie data security and privacy findingsdetective:Get*,detective:List*- Amazon Detective security investigation datasecurityhub:Get*,securityhub:List*- AWS Security Hub consolidated security findingsaccessanalyzer:Get*,accessanalyzer:List*- IAM Access Analyzer findingsconfig:Describe*,config:Get*,config:List*- AWS Config compliance and configuration datacloudtrail:Describe*,cloudtrail:Get*,cloudtrail:List*- CloudTrail audit logs and events
Web Application Firewall
waf:Get*,waf:List*- Classic WAF rules and configurationswafv2:Get*,wafv2:List*,wafv2:Describe*- WAFv2 web ACLs and ruleswaf-regional:Get*,waf-regional:List*,waf-regional:Describe*- Regional WAF configurationsshield:Describe*,shield:Get*,shield:List*- AWS Shield DDoS protection status
Analytics and Machine Learning
glue:Get*,glue:List*- AWS Glue ETL job and catalog metadataathena:Get*,athena:List*- Amazon Athena query execution and resultskinesis:Describe*,kinesis:Get*,kinesis:List*- Kinesis data streaming servicesfirehose:Describe*,firehose:List*- Kinesis Data Firehose delivery streamssagemaker:Describe*,sagemaker:Get*,sagemaker:List*- SageMaker ML model and endpoint datacomprehend:Describe*,comprehend:Get*,comprehend:List*- Amazon Comprehend NLP analysistranslate:Describe*,translate:Get*,translate:List*- Amazon Translate language translationpolly:Describe*,polly:Get*,polly:List*- Amazon Polly text-to-speech synthesisrekognition:Describe*,rekognition:Get*,rekognition:List*- Amazon Rekognition image analysistextract:Get*- Amazon Textract document analysistranscribe:Get*,transcribe:List*- Amazon Transcribe speech-to-text
Application and Workflow Services
states:Describe*,states:Get*,states:List*- AWS Step Functions workflow dataapigateway:GET- API Gateway REST API configurations (read-only HTTP GET)application-insights:Describe*,application-insights:Get*,application-insights:List*- Application performance monitoringxray:Get*,xray:BatchGet*- AWS X-Ray distributed tracing data
Storage and Backup
backup:Describe*,backup:Get*,backup:List*- AWS Backup job status and recovery pointsglacier:Describe*,glacier:Get*,glacier:List*- Amazon Glacier archive storagestoragegateway:Describe*,storagegateway:List*- AWS Storage Gateway hybrid storagedatasync:Describe*,datasync:List*- AWS DataSync data transfer taskstransfer:Describe*,transfer:List*- AWS Transfer Family file transfer protocols
Enterprise and Productivity
workspaces:Describe*,workspaces:List*- Amazon WorkSpaces virtual desktopsappstream:Describe*,appstream:List*- Amazon AppStream 2.0 application streamingworkdocs:Describe*,workdocs:Get*- Amazon WorkDocs document collaborationworkmail:Describe*,workmail:Get*,workmail:List*- Amazon WorkMail email serviceconnect:Describe*,connect:Get*,connect:List*- Amazon Connect contact centerchime:Get*,chime:List*- Amazon Chime communications service
Communication and Messaging
pinpoint:Get*,pinpoint:List*- Amazon Pinpoint customer engagementses:Describe*,ses:Get*,ses:List*- Amazon SES email service configurationsns:Get*,sns:List*- Amazon SNS notification topics and subscriptions
Identity and Cognitive Services
cognito-idp:Describe*,cognito-idp:Get*,cognito-idp:List*- Amazon Cognito user poolscognito-identity:Describe*,cognito-identity:Get*,cognito-identity:List*- Cognito identity pools
IoT and Edge Computing
iot:Describe*,iot:Get*,iot:List*- AWS IoT device and rule configurationsgreengrass:Get*,greengrass:List*- AWS IoT Greengrass edge computing
Media Services
mediaconvert:Describe*,mediaconvert:Get*,mediaconvert:List*- AWS Elemental MediaConvertmediastore:Describe*,mediastore:Get*,mediastore:List*- AWS Elemental MediaStoremediatailor:Describe*,mediatailor:Get*,mediatailor:List*- AWS Elemental MediaTailor
Developer Tools and Code Services
codecommit:BatchDescribe*,codecommit:BatchGet*,codecommit:Describe*,codecommit:Get*,codecommit:GitPull,codecommit:List*- AWS CodeCommit repository access
Cost and Resource Management
pricing:Describe*,pricing:Get*,pricing:List*- AWS Pricing API for cost informationbudgets:Describe*,budgets:View*- AWS Budgets cost and usage trackingce:Describe*,ce:Get*,ce:List*- AWS Cost Explorer cost analysiscur:Describe*,cur:Get*- AWS Cost and Usage Reportstag:Get*- Resource tagging informationresource-groups:Get*,resource-groups:List*,resource-groups:Search*- AWS Resource Groups
Support and Management
support:Describe*,support:Get*,support:List*- AWS Support case and service informationtrustedadvisor:Describe*,trustedadvisor:Get*,trustedadvisor:List*- AWS Trusted Advisor recommendationshealth:Describe*,health:Get*,health:List*- AWS Health Dashboard service statuswellarchitected:Get*,wellarchitected:List*- AWS Well-Architected Tool reviewsservicecatalog:Describe*,servicecatalog:Get*,servicecatalog:List*- AWS Service Catalog products
AI and ML Services
bedrock:Get*,bedrock:List*,bedrock:Describe*- Amazon Bedrock foundation models
CloudFormation
cloudformation:EstimateTemplateCost- Estimating CloudFormation template costscloudformation:ValidateTemplate- Validating CloudFormation template syntax
Security Considerations
⚠️ High-Risk Permissions: Many permissions use wildcard (*) access, granting full control over services. This provides maximum flexibility but requires careful monitoring and access control.
GCP - Integration Permission
Overview
This module creates a GCP Service Account with configurable IAM roles to facilitate AWS-to-GCP Workload Identity Federation. The module supports two permission modes:
- Read-Only Access (
readonly_access = true) - For monitoring, auditing, and discovery workloads - Admin Access (
readonly_access = false) - For infrastructure provisioning and management workloads
Permission Modes
Read-Only Access Mode
- Resource discovery and inventory
- Monitoring and observability workloads
- Audit and compliance scanning
- Non-destructive operations
- Development and testing environments
Read/Write Mode
- Infrastructure provisioning and management
- GKE cluster creation and configuration
- Resource lifecycle management (create, update, delete)
- Production deployments
- Full infrastructure automation
Read-Only Roles
Core Project Access
roles/viewer
Purpose: Provides read-only access to all resources in the project
Permissions Include:
- List and describe all GCP resources
- View project metadata and configuration
- Read IAM policies (but not modify)
- Access monitoring metrics and logs
- View billing information
Use Cases:
- Overall project visibility and inventory
- Compliance auditing and reporting
- Resource discovery across all services
- Cost analysis and optimization
Compute Engine
roles/compute.viewer
Purpose: Read-only access to Compute Engine resources
Permissions Include:
compute.instances.list- List all VM instancescompute.instances.get- Get VM instance detailscompute.disks.list- List persistent diskscompute.disks.get- Get disk configurationcompute.images.list- List available imagescompute.snapshots.list- List disk snapshotscompute.machineTypes.list- List available machine typescompute.zones.list- List available zonescompute.regions.list- List available regions
Use Cases:
- VM inventory and capacity planning
- Disk usage analysis and optimization
- Resource utilization monitoring
- Compliance scanning for compute resources
roles/compute.networkViewer
Purpose: Read-only access to networking resources
Permissions Include:
compute.networks.list- List VPC networkscompute.networks.get- Get network configurationcompute.subnetworks.list- List subnetscompute.subnetworks.get- Get subnet detailscompute.firewalls.list- List firewall rulescompute.firewalls.get- Get firewall rule detailscompute.routes.list- List routescompute.addresses.list- List IP addressescompute.routers.list- List Cloud Routerscompute.vpnGateways.list- List VPN gateways
Use Cases:
- Network topology visualization
- Security posture assessment
- Network connectivity troubleshooting
- IP address management and planning
- VPN and interconnect monitoring
Google Kubernetes Engine (GKE)
roles/container.clusterViewer
Purpose: Read-only access to GKE clusters
Permissions Include:
container.clusters.list- List all GKE clusterscontainer.clusters.get- Get cluster configurationcontainer.clusters.getCredentials- Get cluster credentials for kubectl accesscontainer.operations.list- List cluster operationscontainer.operations.get- Get operation detailscontainer.nodePools.list- List node poolscontainer.nodePools.get- Get node pool configuration
Use Cases:
- GKE cluster inventory and discovery
- Cluster configuration auditing
- Node pool capacity planning
- Kubernetes version compliance checking
- Cluster health monitoring
Cloud Storage
roles/storage.objectViewer
Purpose: Read-only access to Cloud Storage objects
Permissions Include:
storage.buckets.list- List storage bucketsstorage.buckets.get- Get bucket configurationstorage.objects.list- List objects in bucketsstorage.objects.get- Download and read objectsstorage.objects.getIamPolicy- View object-level IAM policies
Use Cases:
- Storage inventory and capacity analysis
- Data location and compliance verification
- Backup and archive monitoring
- Storage cost optimization
- Configuration file retrieval
Cloud SQL
roles/cloudsql.viewer
Purpose: Read-only access to Cloud SQL instances
Permissions Include:
cloudsql.instances.list- List database instancescloudsql.instances.get- Get instance configurationcloudsql.databases.list- List databasescloudsql.databases.get- Get database metadatacloudsql.backupRuns.list- List backup runscloudsql.backupRuns.get- Get backup details
Use Cases:
- Database inventory and discovery
- Backup compliance verification
- Database configuration auditing
- High availability monitoring
- Capacity planning
Cloud KMS
roles/cloudkms.viewer
Purpose: Read-only access to encryption keys
Permissions Include:
cloudkms.keyRings.list- List key ringscloudkms.keyRings.get- Get key ring detailscloudkms.cryptoKeys.list- List encryption keyscloudkms.cryptoKeys.get- Get key configurationcloudkms.cryptoKeyVersions.list- List key versionscloudkms.cryptoKeyVersions.get- Get key version details
Use Cases:
- Encryption key inventory
- Key rotation compliance checking
- Security posture assessment
- Key usage auditing
- Compliance reporting (CMEK verification)
Cloud DNS
roles/dns.reader
Purpose: Read-only access to Cloud DNS
Permissions Include:
dns.managedZones.list- List DNS zonesdns.managedZones.get- Get zone configurationdns.resourceRecordSets.list- List DNS recordsdns.resourceRecordSets.get- Get record detailsdns.changes.list- List DNS changesdns.changes.get- Get change details
Use Cases:
- DNS configuration auditing
- Domain inventory management
- DNS record verification
- DNSSEC compliance checking
- Troubleshooting DNS issues
Secret Manager
roles/secretmanager.secretAccessor
Purpose: Access to read secret values
Permissions Include:
secretmanager.secrets.list- List secretssecretmanager.secrets.get- Get secret metadatasecretmanager.versions.list- List secret versionssecretmanager.versions.access- Access secret valuessecretmanager.versions.get- Get version details
Use Cases:
- Retrieve configuration secrets
- Access application credentials
- Read service account keys
- Retrieve API keys and tokens
- Access database passwords
Security Note: This role grants access to sensitive data. Use with appropriate attribute conditions and audit logging.
Monitoring and Logging (Write Access)
roles/logging.logWriter
Purpose: Write logs to Cloud Logging
Permissions Include:
logging.logEntries.create- Write log entrieslogging.logEntries.route- Route logs to sinks
Use Cases:
- Application logging from AWS workloads
- Audit trail generation
- Custom metric logging
- Error and exception reporting
- Operational telemetry
Note: This is a write permission included in read-only mode to enable observability.
roles/monitoring.metricWriter
Purpose: Write custom metrics to Cloud Monitoring
Permissions Include:
monitoring.timeSeries.create- Write custom metricsmonitoring.metricDescriptors.create- Create custom metric definitionsmonitoring.metricDescriptors.list- List metric descriptors
Use Cases:
- Custom application metrics
- Performance monitoring
- SLO/SLI tracking
- Business metrics reporting
- Health check reporting
Note: This is a write permission included in read-only mode to enable observability.
Admin Roles (admin_roles)
These roles are assigned when readonly_access = false. They provide full administrative capabilities for infrastructure management.
IAM and Resource Management
roles/resourcemanager.projectIamAdmin
Purpose: Full control over project-level IAM policies
Permissions Include:
resourcemanager.projects.getIamPolicy- Get project IAM policyresourcemanager.projects.setIamPolicy- Modify project IAM policyresourcemanager.projects.get- Get project details- Complete IAM policy management
Use Cases:
- Grant and revoke IAM permissions
- Service account permission management
- Workload Identity configuration
- Access control automation
- Security policy implementation
Security Note: This is a highly privileged role. Use with strict attribute conditions in production.
roles/iam.serviceAccountAdmin
Purpose: Full control over service accounts
Permissions Include:
iam.serviceAccounts.create- Create new service accountsiam.serviceAccounts.delete- Delete service accountsiam.serviceAccounts.update- Modify service accountsiam.serviceAccounts.get- Get service account detailsiam.serviceAccounts.list- List service accountsiam.serviceAccounts.setIamPolicy- Set service account IAM policyiam.serviceAccounts.getIamPolicy- Get service account IAM policy
Use Cases:
- Service account lifecycle management
- Automated service account provisioning
- Service account permission delegation
- Identity federation setup
- Application identity management
roles/iam.serviceAccountKeyAdmin
Purpose: Manage service account keys
Permissions Include:
iam.serviceAccountKeys.create- Create service account keysiam.serviceAccountKeys.delete- Delete service account keysiam.serviceAccountKeys.get- Get key metadataiam.serviceAccountKeys.list- List keys for service accounts
Use Cases:
- Service account key rotation
- Key lifecycle management
- Security remediation (key deletion)
- Legacy application key provisioning
Security Note: Best practice is to use Workload Identity Federation instead of keys.
roles/iam.serviceAccountUser
Purpose: Impersonate and act as service accounts
Permissions Include:
iam.serviceAccounts.actAs- Use service account to deploy resourcesiam.serviceAccounts.get- Get service account detailsiam.serviceAccounts.getAccessToken- Get short-lived tokens
Use Cases:
- Deploy resources as a service account
- Cloud Run service deployment
- Cloud Functions deployment
- Compute Engine instance creation with service accounts
- GKE workload identity binding
roles/iam.serviceAccountTokenCreator
Purpose: Create OAuth2 access tokens and OpenID Connect ID tokens for service accounts
Permissions Include:
iam.serviceAccounts.getAccessToken- Generate access tokensiam.serviceAccounts.getOpenIdToken- Generate OIDC tokensiam.serviceAccounts.implicitDelegation- Token delegation
Use Cases:
- Programmatic authentication
- Service-to-service authentication
- API access token generation
- OIDC token creation for third-party services
roles/iam.workloadIdentityPoolAdmin
Purpose: Full control over Workload Identity Pools
Permissions Include:
iam.workloadIdentityPools.create- Create identity poolsiam.workloadIdentityPools.delete- Delete identity poolsiam.workloadIdentityPools.update- Modify identity poolsiam.workloadIdentityPools.get- Get pool configurationiam.workloadIdentityPoolProviders.create- Create providersiam.workloadIdentityPoolProviders.delete- Delete providersiam.workloadIdentityPoolProviders.update- Modify providers
Use Cases:
- Workload Identity Federation setup
- Multi-cloud authentication configuration
- Identity provider management
- Federation policy updates
roles/iam.workloadIdentityPoolViewer
Purpose: Read-only access to Workload Identity Pools
Permissions Include:
iam.workloadIdentityPools.get- Get pool detailsiam.workloadIdentityPools.list- List identity poolsiam.workloadIdentityPoolProviders.get- Get provider detailsiam.workloadIdentityPoolProviders.list- List providers
Use Cases:
- Federation configuration auditing
- Identity pool inventory
- Configuration verification
- Troubleshooting federation issues
Compute and Networking
roles/compute.admin
Purpose: Full control over Compute Engine resources
Permissions Include:
- All
roles/compute.viewerpermissions compute.instances.create- Create VM instancescompute.instances.delete- Delete VM instancescompute.instances.start- Start VM instancescompute.instances.stop- Stop VM instancescompute.instances.reset- Reset VM instancescompute.instances.setMetadata- Set instance metadatacompute.instances.setServiceAccount- Assign service accountscompute.disks.create- Create persistent diskscompute.disks.delete- Delete persistent diskscompute.disks.resize- Resize diskscompute.images.create- Create custom imagescompute.images.delete- Delete imagescompute.snapshots.create- Create disk snapshotscompute.snapshots.delete- Delete snapshots
Use Cases:
- VM lifecycle management
- Auto-scaling implementations
- Infrastructure provisioning
- Disaster recovery operations
- Capacity management
roles/compute.networkAdmin
Purpose: Full control over networking resources
Permissions Include:
- All
roles/compute.networkViewerpermissions compute.networks.create- Create VPC networkscompute.networks.delete- Delete VPC networkscompute.networks.update- Modify VPC networkscompute.subnetworks.create- Create subnetscompute.subnetworks.delete- Delete subnetscompute.subnetworks.update- Modify subnetscompute.firewalls.create- Create firewall rulescompute.firewalls.delete- Delete firewall rulescompute.firewalls.update- Modify firewall rulescompute.routes.create- Create routescompute.routes.delete- Delete routescompute.addresses.create- Reserve IP addressescompute.addresses.delete- Release IP addressescompute.routers.create- Create Cloud Routerscompute.vpnGateways.create- Create VPN gateways
Use Cases:
- VPC network provisioning
- Network topology management
- Firewall rule automation
- IP address management
- VPN and interconnect configuration
- Network security policy implementation
Service Usage
roles/serviceusage.serviceUsageAdmin
Purpose: Enable and disable GCP APIs
Permissions Include:
serviceusage.services.enable- Enable APIsserviceusage.services.disable- Disable APIsserviceusage.services.get- Get API statusserviceusage.services.list- List available APIs
Use Cases:
- Automated API enablement during provisioning
- Service quota management
- API usage optimization
- Cost control (disabling unused APIs)
Google Kubernetes Engine (GKE)
roles/container.admin
Purpose: Full control over GKE clusters
Permissions Include:
- All
roles/container.clusterViewerpermissions container.clusters.create- Create GKE clusterscontainer.clusters.delete- Delete GKE clusterscontainer.clusters.update- Modify cluster configurationcontainer.clusters.upgrade- Upgrade cluster versionscontainer.nodePools.create- Create node poolscontainer.nodePools.delete- Delete node poolscontainer.nodePools.update- Modify node poolscontainer.operations.get- Get operation status- Full Kubernetes API access via cluster credentials
Use Cases:
- GKE cluster lifecycle management
- Cluster version upgrades
- Node pool scaling and management
- Cluster configuration updates
- Infrastructure as Code for Kubernetes
- Production cluster operations
Security Note: This role grants full control over Kubernetes clusters. Combine with attribute conditions for production use.
Cloud Storage
roles/storage.admin
Purpose: Full control over Cloud Storage
Permissions Include:
- All
roles/storage.objectViewerpermissions storage.buckets.create- Create storage bucketsstorage.buckets.delete- Delete storage bucketsstorage.buckets.update- Modify bucket configurationstorage.buckets.setIamPolicy- Set bucket IAM policiesstorage.objects.create- Upload objectsstorage.objects.delete- Delete objectsstorage.objects.update- Modify object metadatastorage.objects.setIamPolicy- Set object-level IAM policies- Complete lifecycle policy management
- Complete bucket policy management
Use Cases:
- Bucket lifecycle management
- Object storage for applications
- Terraform state storage
- Backup and archive management
- Data lake implementation
- Static website hosting
Cloud SQL
roles/cloudsql.admin
Purpose: Full control over Cloud SQL instances
Permissions Include:
- All
roles/cloudsql.viewerpermissions cloudsql.instances.create- Create database instancescloudsql.instances.delete- Delete database instancescloudsql.instances.update- Modify instance configurationcloudsql.instances.restart- Restart instancescloudsql.databases.create- Create databasescloudsql.databases.delete- Delete databasescloudsql.databases.update- Modify databasescloudsql.users.create- Create database userscloudsql.users.delete- Delete database userscloudsql.backupRuns.create- Create backupscloudsql.backupRuns.delete- Delete backups- Complete failover configuration
Use Cases:
- Database provisioning and deprovisioning
- High availability configuration
- Backup and recovery operations
- Database scaling and optimization
- User and access management
Cloud KMS
roles/cloudkms.admin
Purpose: Full control over encryption keys
Permissions Include:
- All
roles/cloudkms.viewerpermissions cloudkms.keyRings.create- Create key ringscloudkms.cryptoKeys.create- Create encryption keyscloudkms.cryptoKeys.update- Modify key configurationcloudkms.cryptoKeyVersions.create- Create key versionscloudkms.cryptoKeyVersions.destroy- Destroy key versionscloudkms.cryptoKeys.setIamPolicy- Set key access policies- Key rotation management
- CMEK configuration
Use Cases:
- Encryption key lifecycle management
- Customer-managed encryption key (CMEK) setup
- Key rotation automation
- Encryption policy implementation
- Compliance requirements (data encryption at rest)
- etcd encryption for GKE
Security Note: KMS admin access is highly sensitive. Enable audit logging and use attribute conditions.
Cloud DNS
roles/dns.admin
Purpose: Full control over Cloud DNS
Permissions Include:
- All
roles/dns.readerpermissions dns.managedZones.create- Create DNS zonesdns.managedZones.delete- Delete DNS zonesdns.managedZones.update- Modify zone configurationdns.resourceRecordSets.create- Create DNS recordsdns.resourceRecordSets.delete- Delete DNS recordsdns.resourceRecordSets.update- Modify DNS recordsdns.changes.create- Create change requests- DNSSEC configuration
Use Cases:
- DNS zone provisioning
- DNS record automation
- Domain management
- Service discovery configuration
- Load balancer DNS integration
- Certificate validation (DNS-01 challenge)
Binary Authorization
roles/binaryauthorization.attestorsAdmin
Purpose: Manage Binary Authorization attestors
Permissions Include:
binaryauthorization.attestors.create- Create attestorsbinaryauthorization.attestors.delete- Delete attestorsbinaryauthorization.attestors.update- Modify attestorsbinaryauthorization.attestors.get- Get attestor detailsbinaryauthorization.attestors.list- List attestorsbinaryauthorization.attestors.verifyImageAttested- Verify attestations
Use Cases:
- Container image security policy enforcement
- Continuous verification of container images
- Supply chain security implementation
- Attestation-based deployment controls
roles/binaryauthorization.policyAdmin
Purpose: Manage Binary Authorization policies
Permissions Include:
binaryauthorization.policy.get- Get policy configurationbinaryauthorization.policy.update- Modify security policiesbinaryauthorization.policy.getIamPolicy- Get IAM policybinaryauthorization.policy.setIamPolicy- Set IAM policy
Use Cases:
- Security policy configuration
- Deployment restrictions based on attestations
- Compliance enforcement for container deployments
- Vulnerability scanning requirements
Secret Manager
roles/secretmanager.admin
Purpose: Full control over secrets
Permissions Include:
- All
roles/secretmanager.secretAccessorpermissions secretmanager.secrets.create- Create secretssecretmanager.secrets.delete- Delete secretssecretmanager.secrets.update- Modify secret metadatasecretmanager.versions.add- Add new secret versionssecretmanager.versions.destroy- Destroy secret versionssecretmanager.versions.disable- Disable secret versionssecretmanager.versions.enable- Enable secret versionssecretmanager.secrets.setIamPolicy- Set secret access policies
Use Cases:
- Secret lifecycle management
- Credential rotation automation
- Secret provisioning for applications
- Sensitive configuration management
- Integration with GKE Secret Manager add-on
Security Note: This role grants full control over secrets. Use with audit logging and strict access controls.
Monitoring and Logging
roles/logging.logWriter
Purpose: Write logs to Cloud Logging (included in both modes)
See Read-Only Roles section above for details.
roles/monitoring.metricWriter
Purpose: Write custom metrics to Cloud Monitoring (included in both modes)
See Read-Only Roles section above for details.
Custom IAM Bindings
The module supports custom IAM bindings via the custom_iam_bindings variable for fine-grained resource-level permissions.
Example: Conditional Access
custom_iam_bindings = [
{
resource = "projects/my-project"
role = "roles/storage.objectViewer"
members = ["serviceAccount:example@project.iam.gserviceaccount.com"]
condition = {
title = "Business hours access"
description = "Only allow access during business hours"
expression = "request.time.getHours() >= 9 && request.time.getHours() <= 17"
}
}
]
Use Cases:
- Time-based access restrictions
- Resource-specific permissions
- Temporary access grants
- Compliance-driven access controls
Security Best Practices
1. Principle of Least Privilege
- Start with read-only access and add permissions as needed
- Use
readonly_access = truefor non-production environments - Document why each permission is required
2. Attribute Conditions
Use attribute conditions to restrict federation based on AWS identity attributes:
attribute_condition = "attribute.aws_role.startsWith('Production-') && attribute.aws_account == '123456789012'"
Examples:
- Restrict by AWS role name
- Restrict by AWS account ID
- Restrict by time of day
- Combine multiple conditions
3. Audit Logging
Always enable audit logging in production:
enable_audit_logs = true
Monitors:
- Token generation requests
- Service account impersonation
- Permission usage
- Failed authentication attempts
4. Multi-Account Strategy
Use separate service accounts for different AWS accounts or security tiers:
# Production federation (read-only)
module "prod_federation" {
aws_account_ids = ["123456789012"]
readonly_access = true
}
# Development federation (admin access)
module "dev_federation" {
aws_account_ids = ["123456789999"]
readonly_access = false
}
5. Regular Access Reviews
- Quarterly review of assigned roles
- Remove unused or excessive permissions
- Update attribute conditions as requirements change
- Monitor audit logs for anomalous access patterns
6. Labels and Tagging
Use comprehensive labels for governance:
labels = {
environment = "production"
team = "platform"
security_tier = "high"
compliance = "sox-gdpr"
cost_center = "engineering"
}
Workload Identity Federation Permissions
The module itself requires permissions to create federation resources. The Terraform service account needs:
Required Terraform Permissions
roles/iam.workloadIdentityPoolAdmin:
- Create and manage Workload Identity Pools
- Configure identity providers (AWS)
- Set attribute mappings and conditions
roles/iam.serviceAccountAdmin:
- Create the federated service account
- Configure service account IAM policies
- Grant workloadIdentityUser role
roles/resourcemanager.projectIamAdmin:
- Bind roles to the service account
- Configure project-level IAM policies
Setup Script
# Create Terraform service account
gcloud iam service-accounts create terraform-federation \
--display-name="Terraform Federation Service Account"
# Grant required permissions
for role in roles/iam.workloadIdentityPoolAdmin \
roles/iam.serviceAccountAdmin \
roles/resourcemanager.projectIamAdmin; do
gcloud projects add-iam-policy-binding PROJECT_ID \
--member="serviceAccount:terraform-federation@PROJECT_ID.iam.gserviceaccount.com" \
--role="$role"
done
# Create and export credentials
gcloud iam service-accounts keys create terraform-sa-key.json \
--iam-account=terraform-federation@PROJECT_ID.iam.gserviceaccount.com
export GOOGLE_CREDENTIALS=$(cat terraform-sa-key.json)
Monitoring and Alerting
Key Metrics to Monitor
-
Federation Token Requests
- Monitor for unusual spikes in token generation
- Alert on failed authentication attempts
-
Permission Usage
- Track which permissions are actively used
- Identify unused permissions for removal
-
Service Account Activity
- Monitor API calls made by the federated service account
- Alert on access to sensitive resources
-
Audit Log Patterns
- Track changes to IAM policies
- Monitor modifications to the identity pool
- Alert on workload identity pool disablement
Sample Alert Query
resource.type="iam_workload_identity_pool"
protoPayload.methodName="GenerateAccessToken"
severity="ERROR"
Compliance Considerations
SOX Compliance
- Enable comprehensive audit logging
- Implement proper access controls and reviews
- Maintain audit trails for all federation activities
- Regular compliance assessments
GDPR Compliance
- Ensure proper data handling in cross-cloud scenarios
- Implement data residency controls if required
- Maintain records of data processing activities
- Enable audit logging for data access
Industry Standards
- Follow NIST Cybersecurity Framework
- Implement CIS Controls for cloud security
- Regular security assessments and penetration testing
- Incident response procedures for federation issues
Troubleshooting
Permission Denied Errors
-
Verify Role Assignment
gcloud projects get-iam-policy PROJECT_ID \ --flatten="bindings[].members" \ --filter="bindings.members:serviceAccount:SERVICE_ACCOUNT_EMAIL" -
Check Attribute Conditions
- Verify AWS role name matches attribute condition
- Ensure AWS account ID is in the allowed list
- Test attribute mapping with sample AWS identities
-
Review Audit Logs
gcloud logging read "resource.type=iam_workload_identity_pool" \ --limit 50 \ --format json
Insufficient Permissions
If you encounter "insufficient permissions" errors:
- Add required roles to
readonly_rolesoradmin_rolesinterraform.tfvars - Apply the Terraform changes to update service account permissions
- Wait 60-120 seconds for IAM changes to propagate
- Retry the operation